What is IDS and IPS?
Problems IDS/IPS AddressA typical business network has several access points to other networks, both public and private. The challenge is maintaining the security of these networks while keeping them open to their customers. Currently, attacks are so sophisticated that they can thwart the best security systems, especially those that still operate under the assumption that networks can be secured by encryption or firewalls. Unfortunately, those technologies alone are not sufficient to counter today’s attacks.
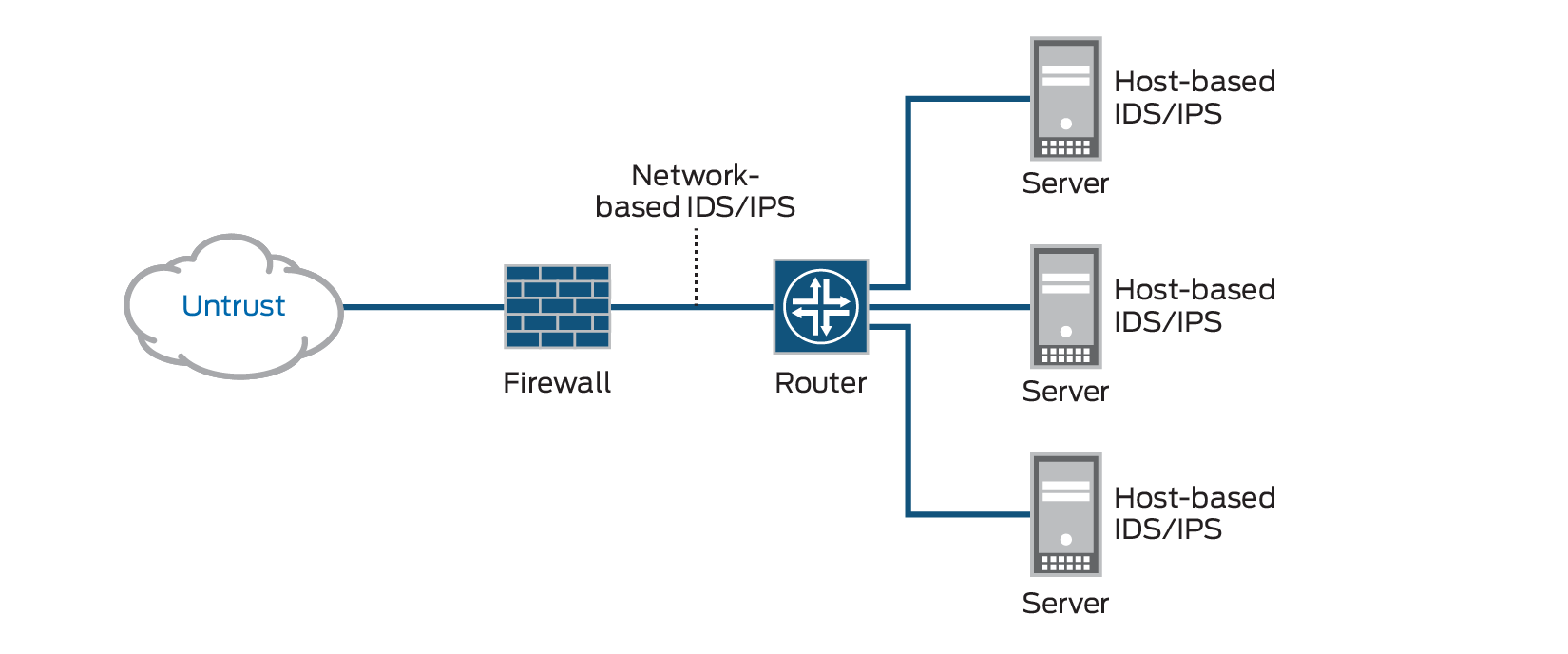
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) constantly watch your network, identifying possible incidents and logging information about them, stopping the incidents, and reporting them to security administrators. In addition, some networks use IDS/IPS for identifying problems with security policies and deterring individuals from violating security policies. IDS/IPS have become a necessary addition to the security infrastructure of most organizations, precisely because they can stop attackers while they are gathering information about your network.
The three IDS detection methodologies are typically used to detect incidents.
Juniper Networks uses its SRX Series Services Gateways for intrusion detection and prevention (IDP) services. You can selectively enforce various attack detection and prevention techniques on the network traffic passing through your chosen SRX Series device. You can define policy rules to match a section of traffic based on a zone, a network, or an application, and then take active or passive preventative actions on that traffic. The SRX Series device contains a full set of IPS signatures to secure networks against attacks. Juniper Networks regularly updates the predefined attack database. The SRX Series device can forward packet capture (PCAP) data from its traffic to a Juniper Secure Analytics (JSA) appliance using the PCAP Syslog Combination Protocol.
- @ Copyright 2020 Acronics
